CS707 Newtork Security Short Question - Differentiate between private and secret key
1. Differentiate between private and secret key.
The secret key is used in symmetric cryptography where only one key is needed for encryption and decryption
Private and public key are the two keys that two different entities are using in public key cryptography to decrypt (using the private) what have been encrypted with the public or reverse.
Private and public key are the two keys that two different entities are using in public key cryptography to decrypt (using the private) what have been encrypted with the public or reverse.
2. What are main components of Kerberos?
When using the Kerberos protocol, a Key Distribution Center (KDC) is used to store, distribute, and maintain cryptographic session and secret keys.
Kerberos Software Components
The Athena implementation comprises several modules:
- Kerberos applications library
- encryption library
- database library
- database administration programs
- administration server
- authentication server
- DB propagation software
- user programs
- applications
3. What is an asymmetric key algorithm
Symmetric vs. asymmetric algorithms
When using symmetric algorithms, both parties share the same key for en- and decryption. To provide privacy, this key needs to be kept secret. Once somebody else gets to know the key, it is not safe anymore. Symmetric algorithms have the advantage of not consuming too much computing power. A few well-known examples are DES, Triple-DES (3DES), IDEA, CAST5, BLOWFISH, TWOFISH.
Asymmetric algorithms use pairs of keys. One is used for encryption and the other one for decryption. The decryption key is typically kept secretly, therefore called ``private key'' or ``secret key'', while the encryption key is spread to all who might want to send encrypted messages, therefore called ``public key''. Everybody having the public key is able to send encrypted messages to the owner of the secret key. The secret key can't be reconstructed from the public key. The idea of asymmetric algorithms was first published in 1976 by Diffie and Hellmann.
Strengths & Weaknesses Of Asymmetric Encryption
Strengths
• Better key distribution than symmetric systems
• Better scalability than symmetric systems
• Can provide authentication and non-repudiation
Weaknesses
• Works much more slowly than symmetric systems
Mathematically intensive tasks
4. What are the main component of symmetric encryptions? Describe its limitations.
( unsolved )
Long Questions
1. What are Characteristics Of Strong Stream Ciphers?
Characteristics Of Strong Stream Ciphers
• Long periods of no repeating patterns within keystream values
– Bits generated by the keystream must be random
• Statistically unpredictable keystream
– The bits generated from the keystream generator cannot be predicted
• A keystream not linearly related to the key
– If someone figures out the keystream values, that does not mean she now knows the key value
• Statistically unbiased keystream (as many 0’s as 1’s)
– There should be no dominance in the number of 0’s or 1’s in the keystream
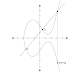
2. What is ECC algorithm.
An elliptic curve cryptosystem (ECC) provides much of the same functionality RSA provides: digital signatures, secure key distribution, and encryption. One differing factor is ECC’s efficiency.
Elliptic Curves
In this field of mathematics, points on the curves compose a structure called a group.

Elliptic Curve Cryptosystems
The Figure is an example of an elliptic curve. In this field of mathematics, points on the curves compose a structure called a group. These points are the values used in mathematical formulas for ECC’s encryption and decryption processes.
The algorithm computes discrete logarithms of elliptic curves, which is different from calculating discrete logarithms in a finite field (which is what Diffie-Hellman and El Gamal use).
Some devices have limited processing capacity, storage, power supply, and bandwidth such as wireless devices and cellular telephones. With these types of devices, the efficiency of resource use is very important.
ECC provides encryption functionality, requiring a smaller percentage of the resources needed by RSA and other algorithms, so it is used in these types of devices.
In most cases, the longer the key, the more protection that is provided, but ECC can provide the same level of protection with a key size that is shorter than what RSA requires.
Because longer keys require more resources to perform mathematical tasks, the smaller keys used in ECC require fewer resources of the device.





No comments: